North Korean Hackers Pull off Record $2B Crypto Theft in 2025

- North Korean hackers stole $2B in crypto in 2025, their biggest annual total on record.
- The Bybit hack in February accounted for $1.46B, the largest single crypto theft in history.
- Most attacks used social engineering tactics, replacing traditional code-based exploits.
North Korean state-backed hackers have stolen over $2 billion in crypto in 2025 alone, their largest annual total on record, according to blockchain analytics firm Elliptic. The thefts, including over 30 confirmed incidents across multiple countries, have pushed Pyongyang’s cumulative crypto haul past $6 billion, funding its sanctioned nuclear and missile programs.
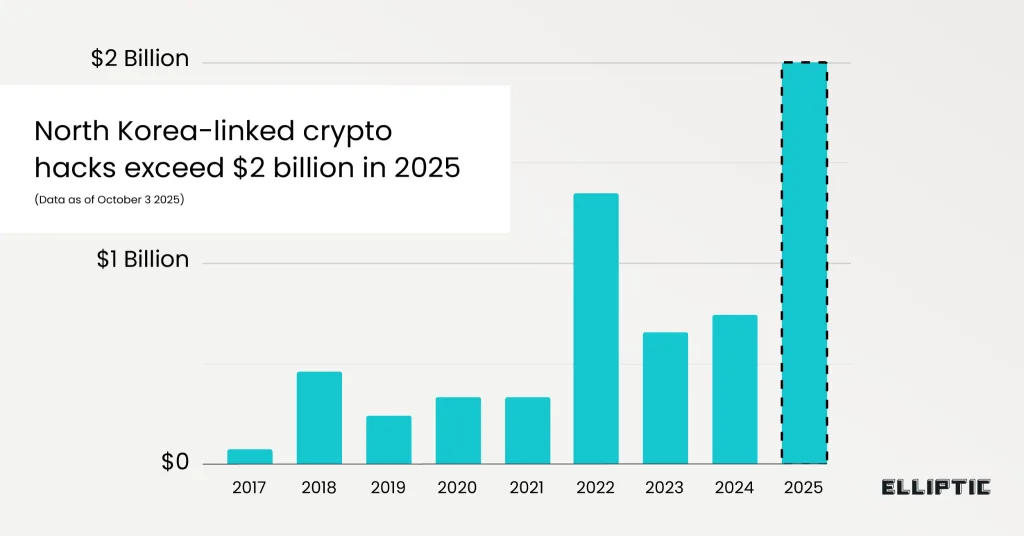
Bybit Hack and Record Year of Cyber Heists
The biggest theft of the year came in February when Dubai-based exchange Bybit lost $1.46 billion in digital assets. According to Elliptic, the attack was carried out by the Lazarus Group, North Korea’s most notorious hacking unit.
The breach, which is the largest single crypto theft ever recorded, tripled North Korea’s 2024 total and broke its 2022 record of $1.35 billion. However, the Bybit incident was only part of a wider pattern. Elliptic attributed at least 30 additional hacks to North Korean groups between January and September 2025.
Among the victims were Taiwan-based WOO X, which lost $14 million in July, and blockchain gaming platform Seedify, which lost $1.2 million in September. These operations show the regime’s growing reliance on cyber-enabled theft to bypass international sanctions.
The attacks, experts noted, collectively account for nearly 13% of North Korea’s gross domestic product, based on United Nations estimates. U.S., Japanese, and South Korean authorities have repeatedly linked such thefts to Pyongyang’s weapons development efforts, identifying crypto as the regime’s most profitable source of foreign revenue.
Human Weakness Now Replaces Code Vulnerabilities
Unlike previous years dominated by code-based exploits, most 2025 breaches have relied on deception. Elliptic found that North Korean hackers changed focus toward social engineering, tricking people into giving access rather than breaking systems.
This tactic has allowed attackers to target high-net-worth individuals who lack the security infrastructure of large exchanges. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the FBI have issued multiple advisories describing how North Korean actors pose as crypto engineers or project collaborators.
Using fake job offers, they deliver malware-laced “test projects” and wallet tools designed to steal credentials and compromise systems. These strategies draw on earlier malware families such as AppleJeus and TraderTraitor, both tied to the Lazarus Group.
This change indicates a new vulnerability in the crypto market. The weak link is no longer faulty code but the individual behind the keyboard. As crypto adoption grows, the increasing number of potential victims provides more opportunities for social manipulation.
Laundering Techniques More Complex
Once assets are stolen, North Korean operatives move fast to disguise their origin. Elliptic described a complicated laundering network that ranges from multiple blockchains and services. Hackers reportedly use chain hopping, obscure tokens, and cross-chain bridges to divide and reroute funds across lesser-known networks.
The Bybit heist, for instance, saw funds go through Bitcoin, Ethereum, BTTC, and Tron chains using at least three bridging protocols. Analysts observed the use of “refund addresses” to redirect funds and the creation of new tokens by laundering groups to make the activity unclear. These measures reduce traceability while lowering transaction costs, enabling fast liquidation in over-the-counter markets that operate with minimal compliance oversight.
To counter this, authorities have intensified enforcement actions. The U.S. Department of Justice convicted Tornado Cash co-founder Roman Storm for running an unlicensed money transmission service used by North Korean hackers in August 2025.
Still, Elliptic warned that attributing such operations is challenging. The firm reported that many thefts share the same behavioral outlook but lack conclusive forensic evidence linking them to Pyongyang. Other cases likely are unreported or undetected, meaning the $2B figure could be an underestimate.
Related: THORChain Co-Founder JP Loses $1.35M to North Korean Phishing Attack
Surveillance and Industry Safeguards
Regulators globally are tightening rules for exchanges, mixers, and custodial wallets to limit exposure. The Financial Action Task Force labeled North Korea the “most severe state-based threat” to crypto markets.
Despite the complicated laundering tactics, blockchain transparency gives investigators an advantage. Every transaction leaves a digital trace that can be followed, allowing forensic teams to identify patterns and block stolen funds before they are cashed out.
Meanwhile, North Korea’s $2 billion crypto theft spree shows a changing means in cybercrime. It also indicates how quickly threat actors adapt, forcing law enforcement, analytics firms, and exchanges to grow just as fast to safeguard the integrity of global crypto markets.




