ZachXBT Tracks $28M Bittensor Hack Through NFT Trades

- ZachXBT traced a $28M hack suspect using anime NFT trades tied to insider wallets.
- The investigation involved the pillaged TAO funds of a former Bittensor engineer.
- Nearly $5M in stolen assets moved via Railgun and Monero, exposing laundering routes.
On October 15, 2025, blockchain investigator ZachXBT revealed how he identified one of the main suspects behind the 2024 $28 million Bittensor hack. In his post on X, he described how anime NFT wash trades led him to a former employee of the project. His findings earned him a whitehat bounty for his assistance in uncovering the identity behind one of the largest crypto thefts of 2024.
On July 3, 2024, the community update of the Opentensor Foundation mentioned that the team had identified suspicious fund flows, and to be on the safe side, the team placed the validators behind a firewall and brought the system to safe mode. Subsequent inquiries revealed that a malicious upload to the PyPI package repository (version 6.12.2) had quietly decrypted users’ cold key data and transferred it to the hacker’s server.
The Bittensor blockchain protocol and Subtensor code, however, remained intact. The Foundation advised users that the wallets and operations had been compromised, but the core system integrity had not been affected.
Linking NFT Wash Trades to the Bittensor Breach
Initially, it was believed that the attack had resulted in the theft of approximately $8 million worth of TAO tokens. The later assessments, among them ZachXBT’s, revealed losses totaling $28 million with 32 TAO holders involved. The research of ZachXBT revealed that the attacker had laundered the money through fake buy-sell trades of overpriced anime-themed NFTs, whose prices were set far above market value.
ZachXBT tracked these transfers back to wallets associated with a previous Bittensor engineer, revealing the use of NFTs as a cover for stolen cryptocurrencies. He meticulously analyzed the transactions on various trading platforms and discovered the loops of the wash trades that had been carried out to conceal the movement of the digital assets. This repetitive pattern not only linked the stolen coins to insiders with privileged access but also offered crucial clues relevant to the ongoing legal investigation.
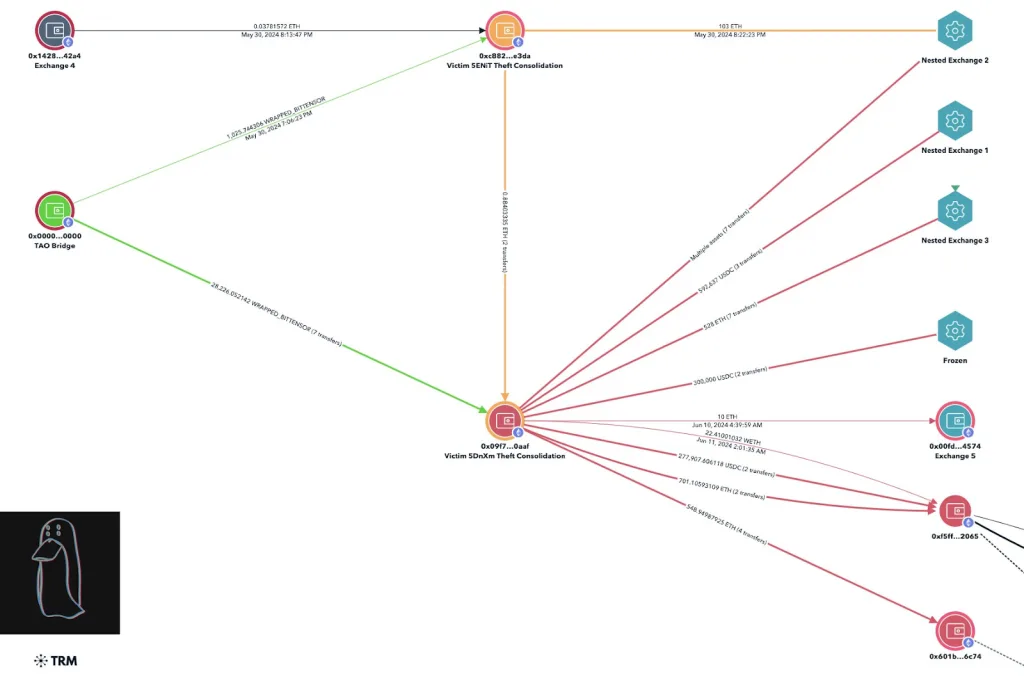
His investigation into the stolen assets did not limit him to NFTs but went as far as following the cross-chain transactions, privacy mixers, and bridge schemes. He tracked suspicious movements of money through the Avalanche bridge and Railgun privacy protocol, where around $4.94 million changed hands before being turned into Monero (XMR). By a meticulous analysis of the time and amount patterns, ZachXBT was able to unveil some of the withdrawal flows from Railgun that coincided with the suspect’s money laundering methods.
Although the NFT portion accounted for about $100,000 of the stolen assets, it became the key that unlocked the broader investigation. According to ZachXBT, cases involving NFT wash trading in crypto hacks are sporadic.
Related: U.S. Court Affirms NFTs Are Not Securities in Yuga Labs Case
Unmasking Internal Risk and Laundering Innovation
The wallet of the suspect, which was linked through several addresses, confirmed insider connections to the Bittensor project. After the disclosure of ZachXBT, the Bittensor team recognized his effort and rewarded him not only with a whitehat bounty but also for aiding in the recovery process.
The Bittensor case made the point that while blockchain protocols might be perfectly secure, the dependencies, such as software packages and employee access, could still become points of exploitation.
The application of anime NFTs as a laundering method has also shown that cybercriminals are getting increasingly creative in hiding stolen crypto. The OpenTensor Foundation’s post-mortem document was a pledge to the public of transparency, but till now, there has been no complete recovery or public attribution confirmed.
The situation remains an archetype of how constant on-chain investigation can reveal even the most intricate cross-chain laundering operations, combining blockchain analysis with forensic-like accuracy.




